Travel agencies have emerged as the target of a hack-for-hire group dubbed Evilnum as part of a broader campaign aimed at legal and financial investment institutions in the Middle East and Europe.
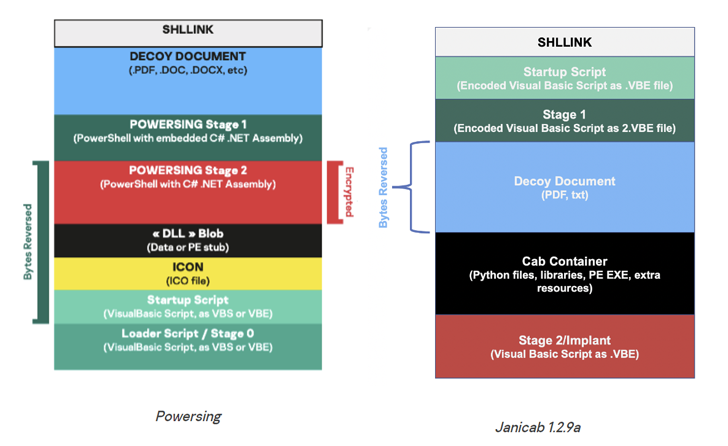
The attacks, which took place during 2020 and 2021 and likely went as far back as 2015, involved a revamped variant of a malware called Janicab that leverages a number of public services like WordPress and YouTube as dead drop resolvers, Kaspersky said in a technical report published this week.
Janicab infections comprise a diverse set of victims located in Egypt, Georgia, Saudi Arabia, the UAE, and the U.K. The development marks the first time legal organizations in Saudi Arabia have been targeted by this group.
Also tracked as DeathStalker, the threat actor is known to deploy backdoors like Janicab, Evilnum, Powering, and PowerPepper to exfiltrate confidential corporate information.
"Their interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as some sort of information broker in financial circles," the Russian cybersecurity company noted in August 2020.
According to ESET, the hacking crew has a pattern of harvesting internal company presentations, software licenses, email credentials, and documents containing customer lists, investments, and trading operations.
Earlier this year, Zscaler and Proofpoint uncovered fresh attacks orchestrated by Evilnum that have been directed against companies in the crypto and fintech verticals since late 2021.
Kaspersky's analysis of the DeathStalker intrusions has revealed the use of an LNK-based dropper embedded inside a ZIP archive for initial access by means of a spear-phishing attack.
The lure attachment purports to be an industrial profile document related to power hydraulics that, when opened, leads to the deployment of the VBScript-based Janicab implant, which is capable of command execution and deploying more tools.
Newer versions of the modular malware have simultaneously removed audio recording features and added a keylogger module that shares overlaps with prior Powersing attacks. Other functions include checking for installed antivirus products and getting a list of processes indicating malware analysis.
The 2021 attacks are also notable for employing unlisted old YouTube links that are used to host an encoded string that's deciphered by Janicab to extract the command-and-control (C2) IP address for retrieving follow-on commands and exfiltrating data.
"Since the threat actor uses unlisted old YouTube links, the likelihood of finding the relevant links on YouTube is almost zero," the researchers said. "This also effectively allows the threat actor to reuse C2 infrastructure."
The findings underscore that the threat actor has continued to update its malware toolset to maintain stealthiness over extended periods of time.
Besides applications allowing a listing and operating system hardening, organizations are recommended to monitor Internet Explorer processes, since the browser is used in hidden mode to communicate with the C2 server.
As legal and financial sectors are a common targets for the threat actor, the researchers further theorized that DeathStalker's customers and operators could be weaponizing the intrusions to keep tabs on lawsuits, blackmail high-profile individuals, track financial assets, and harvest business intelligence about potential mergers and acquisitions.











No record found